
Healthcare IT should listen to Amazon's Werner Vogels: “Dance Like Nobody’s Watching. Encrypt Like Everyone Is”
Security Published on •5 mins Last updatedWhen I heard the above comment from Amazon’s Werner Vogels back in January last year it resonated with me, as I often find myself dealing with complex customer requirements such as securing important customer data. He made the comment while wearing a T-Shirt saying “Encrypt Everything”: something we’re hopefully all now starting to do.
Because of this, today we're going to look at securely moving data around in healthcare which is one of those sensitive environments where securing your data actually matters. Patients’ personal data is incredibly important and nobody would like to think that their data is being stored or shared in an insecure manner.
The start of the issue is that today it's more important than ever to make sure that as much data as possible is being gathered and then kept. This is so that it can be interrogated, searched and used in order to improve our healthcare experience in a whole multitude of ways. Healthcare IT is getting smarter and now even uses Machine Learning and AI techniques, generating training models that lead to predictions which are then used to improve clinical outcomes. This is allowing us to enter a new age of discovery, bringing more knowledge of what really works and what doesn’t as we follow trends and outcomes over time and across huge datasets.
So to the crux of the problem…we have HUGE amounts of data which needs to stay secure! Generally, we have two “states” this data may be in and we need to secure them both: your data is either “at rest”, so stored somewhere, or “in transit”, so being moved somewhere. As such, you first need to provide “encryption at rest”, which is basically encryption of your data on its storage. Then you have “encryption in transit”, which is the act of encrypting data as it moves around the network between devices or even across the WAN. Security is key as we are dealing with private and personal data, which many of us regard as more valuable even than our own financial data! As such, making sure that it remains safe and secure is critical.
Your key security goals should be:
Confidentiality of data
Integrity of data
Authenticity of data
Keeping data secure at rest is as simple as encryption within the storage layer. Making sure that your hard drives and other storage systems are encrypted and password-protected is an easy task, but it's not always as easy to guarantee that data can move securely between your network and it’s final destination, especially when traversing networks that are not fully under your control.

An example of this could be hospitals linked together by a Metronet or even what we find in the UK with the NHS which has the dedicated “Health and Social Care Network (HSCN)” to provide inter-hospital communication for sharing data.
But this network (and others like it) offer no innate, built-in encryption at all! In their defense, though, they do mandate that you use encryption, even stating the level required (AES-256).
So what options exist for “Encryption in transit”? This is where you may look at technologies such as VPNs or indeed TLS.
First, let me say that using a VPN is often the solution, especially if you have lots of different communication that needs to pass between locations securely. With enough use cases, a VPN does become obvious as it is a permanent tunnel (at layer 3) to a fixed destination that can handle many different protocols and users at once. It provides a private network inside the tunnel it creates and then encrypts everything that passes through the tunnel. Its only real drawback is the ongoing maintenance and probably the associated costs.
I want to explore a simpler option where I may only need to move data between one or two specific applications, where we may even have a private (or semi-private) network in place such as our Metronet or HSCN examples. Let’s talk about TLS.
“SSL/TLS with some kind of auth can effectively replace a VPN.”
We all probably use TLS everyday, whether it’s protecting our shopping experiences or securing access to our bank accounts. TLS is a mainstay of securing our online transactions. As such, we can use the same technology to securely move our healthcare data in the same way: creating secure tunnels between endpoints so that you can traverse an insecure network while maintaining the same security offered by credit card systems and banking systems the world over. This can keep costs down by reducing the need to have a complex VPN and the ongoing management that goes with it.
Using TLS to encrypt the specific stream containing our secure data is a solution that’s easy to use and very hard to misuse, however, what about the user auth mentioned above which can help to avoid man-in-the-middle attacks?
This is where we leverage mutual TLS, where client and server are both validated, rather than the traditional security model used by SSL/TLS which only verifies the server and not the client. The server and clients have their own certificates to provide in order to be verified, which ensures not only that data is secure but also that data cannot be injected by bad actors potentially trying to spoil data or inject malware into the system.
Another benefit to mutual TLS is that hospital systems do not need to natively support TLS, meaning that legacy systems can also take advantage of this added security without great expense being wasted on upgrading or replacing legacy systems. What we're looking to create is a point-to-point SSL connection between locations, allowing insecure data to enter the tunnel, be encrypted safely, securely traverse the tunnel and exit on the other side unencrypted. Client and server never know about the encryption.
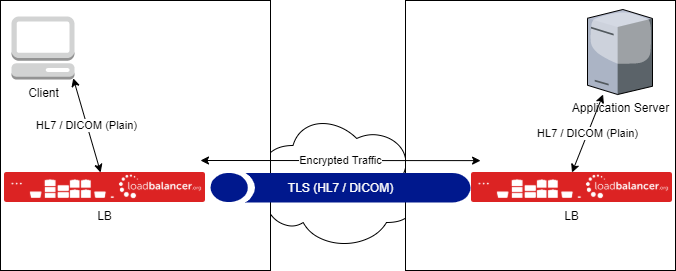
These techniques are going to be extremely important as health care continues to require first class security without extreme costs. We've seen what's happened in the US with the ERP.
We've seen more security required in other systems that we all use and across the Internet at large.
We've seen companies we trust act like bad actors, such as Google and Facebook, who may have shared data when they shouldn't have.
So I think it is ever so important to get this right in healthcare where, as I said at the beginning of this post, it matters the most.
