Load balancing Microsoft Always-On VPN

Useful resources
About Microsoft Always On VPN
Microsoft Always On VPN provides a single, cohesive solution for remote access and supports domain-joined, non domain-joined (workgroup), or Azure AD–joined devices, even personally owned devices.
With Always On VPN, the connection type does not have to be exclusively user or device but can be a combination of both. For example, you could enable device authentication for remote device management and then enable user authentication for connectivity to internal company sites and services.
Key benefits of load balancing
Here are a few key benefits:
- Ensures the application is always available
- Provides a stable, optimal performance
- Ability to isolate servers which reduces risk when performing upgrades/maintenance
- Scalability
Microsoft’s Enterprise solutions are at the heart of businesses everywhere. Loadbalancer.org is officially certified for all of Microsoft’s key applications which you can find here. More details on the Always On components, how it works, and prerequisites for load balancing can be found in our deployment guide, available to view below.
How to load balance Microsoft Always On VPN
We recommend using Layer 4 SNAT mode for Always On VPN. This mode offers good performance and is simple to configure since it requires no configuration changes to the Always On VPN and Network Policy servers. Layer 4 DR mode and NAT mode can also be used if preferred. To use DR mode it is required to solve the ARP problem on each Always On VPN server (please see the Administration Manual and search for “DR mode considerations”). Using NAT mode requires the default gateway on each real server to be configured to be the load balancer.
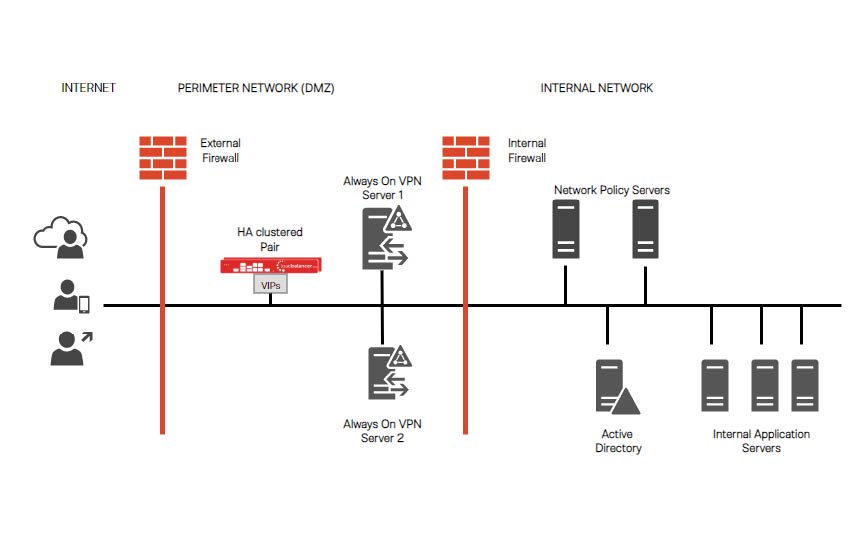 Load balancers can be deployed as single units or as a clustered pair. We recommend deploying a clustered pair for resilience and high availability. Details on configuring a clustered pair can be found on page 19 of our deployment guide, below.
Load balancers can be deployed as single units or as a clustered pair. We recommend deploying a clustered pair for resilience and high availability. Details on configuring a clustered pair can be found on page 19 of our deployment guide, below.
deployment guide

Microsoft Always on VPN Deployment Guide
Read deployment guidemanual

Administration manual v8
Read manualcase studies

Microsoft Exchange - Sunfield Children’s Home
Read case study
Microsoft Dynamics CRM - Melbourne Cricket Club
Read case studyblogs

How Scomis improves the scalability and performance of its Hosted Application Service
Read blog
Enhanced Microsoft IIS health checks using VBscript
Read blog
Load Balancing Exchange 2013
Read blogother

How to load balance Microsoft applications
Read other

