
“Load balancing FTP can be loads of fun for system and network administrators alike!” - said nobody ever.
Implementation of FTP and configuration of your firewalls can be cumbersome, especially when it comes to being secure during your file transfer. The downside to an FTP connection is that the data is generally sent as plain text (usernames and passwords included), and that’s just not acceptable in this day and age. It’s all about security, security, security!
So what options do we have to ensure that our FTP connections are secure? Enter FTPS (file transfer protocol SSL), with a choice of two modes: FTPS implicit and FTPS explicit.
Let’s start with implicit FTPS
When an implicit FTPS connection is started, an SSL connection is instantaneously established over the default port of 990 prior to being granted access to the FTP server. If a secure connection cannot be made then the connection is dropped. Although implicit FTPs is more stringent than explicit mode, it has now been deprecated. Some legacy systems may still make use of it, hence it still being around.
Next we have explicit FTPS
Initiating an explicit FTPS connection is very similar to an unencrypted FTP connection, in that the standard port 21 is used for both methods. The difference is that prior to the connection prompting for a login, the unencrypted connection is upgraded to a secure SSL connection over port 21. Essentially FTPS explicit is FTP requesting to STARTTLS before the connection is granted access to the FTP server.
Explicit FTPS grants users the ability to determine whether their data is forwarded unencrypted - all of the data, or specific items such as usernames and passwords. Additionally, you can configure explicit FTPS to outright drop insecure connections or fallback to the standard FTP protocol, as it’s also using port 21.
How do you load balance implicit and explicit FTPS?
- Create a layer 7 virtual service via the Webui > Cluster Configuration > Layer 7 Virtual Services > Add a new Virtual Service
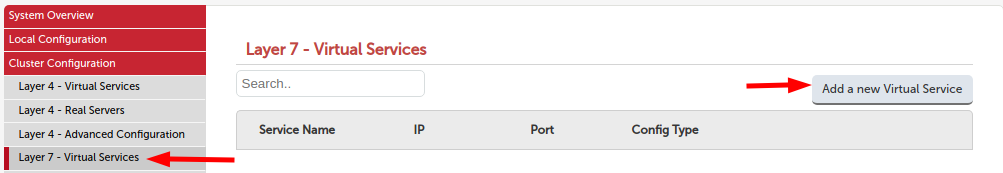
- Label the VIP appropriately in the case FTPS_VIP
- Enter the appropriate IP address that you wish to use as the VIP. In this example I am using 192.168.86.87.
4.Enter ports 21 for explicit FTPS, 990 for implicit FTPS, and finally your passive port range; in this case 1025-1052. - Select TCP mode as the layer 7 protocol
- Click update
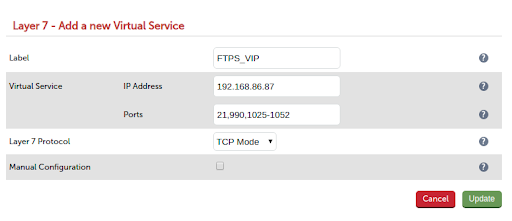
- Next add the real FTP servers to the VIP cluster
- Enter the name of the real server FTP_SVR1
- Enter the IP address of the real server 192.168.86.50
- Click update
- Add any remaining FTP servers to the VIP cluster.
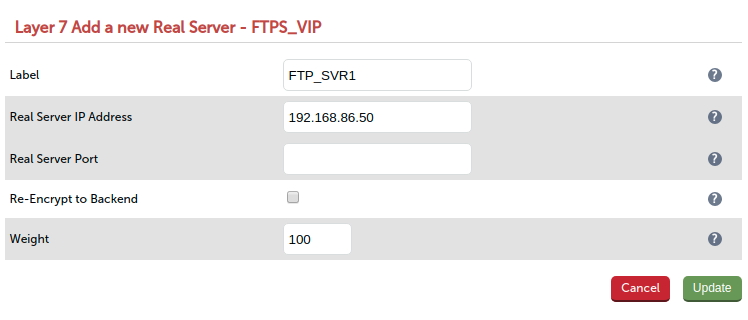
- Reload HAproxy to commit the configuration
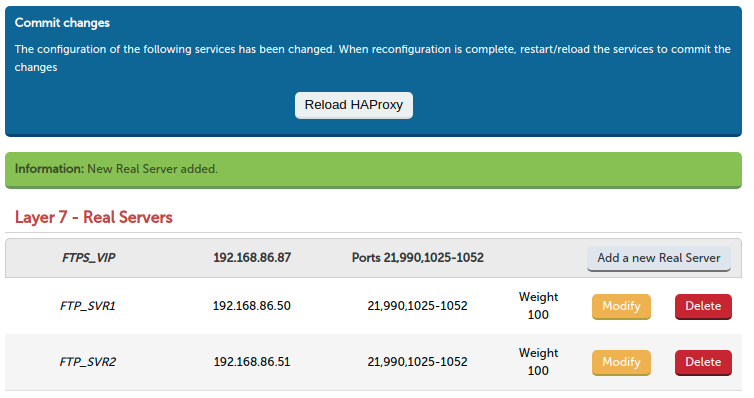
- Next we need to configure our real servers to accept incoming requests from the VIP using the provided passive ports 1025 - 1052. (Please also ensure that you have allowed your firewall to accept TCP traffic on ports 21 and 990).
- On the real server open IIS Manager and on the top level server go to FTP Firewall Support.
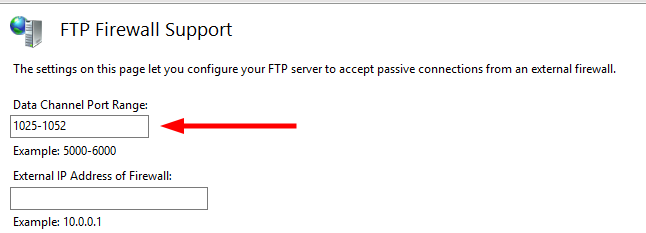
- Enter your passive port range 1025 - 1052 and click apply
- Click on the FTP site (in this example it is the Default FTP Site) and select FTP Firewall Support. Enter the VIP address we are using on the load balancer 192.168.86.87 and click apply.
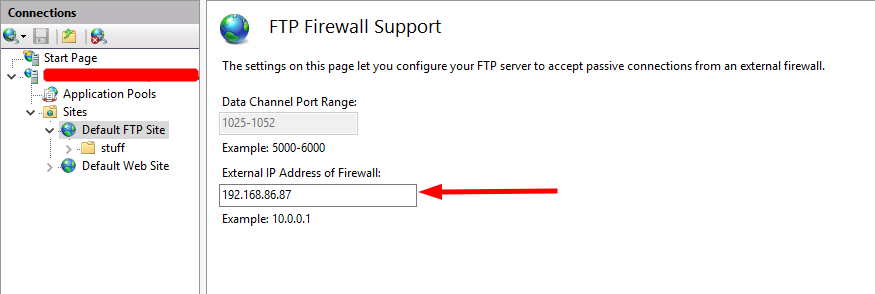
-
Enter the VIP address we are using on the load balancer 192.168.86.87 and click apply.
-
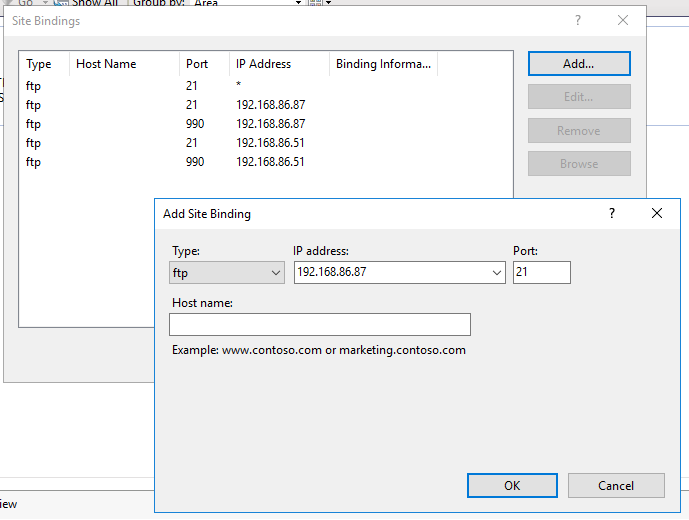
Next we need to edit our site bindings to listen to the VIP and ports 21 and 990 that we have configured on the load balancer.
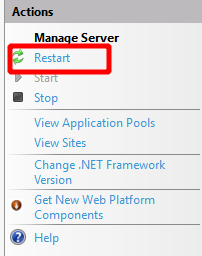
- We need to restart the IIS server at the top level via Actions > Manage Server > Restart
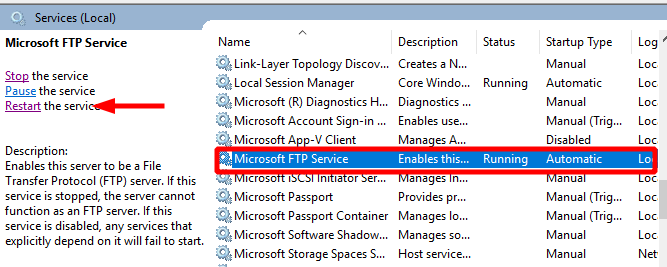
- Finally we need to restart the FTP service to ensure that the configuration is now committed.
- All that is left to do now is test that we can connect to our FTP servers via the load balancer. I will be using Winscp for my client in this test.
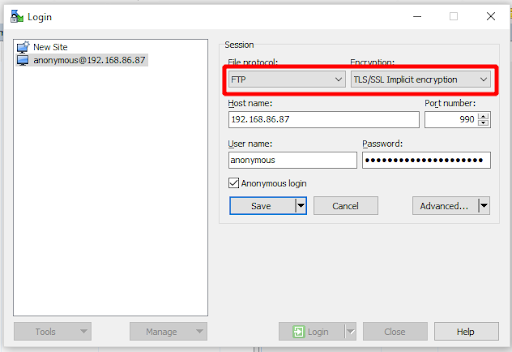
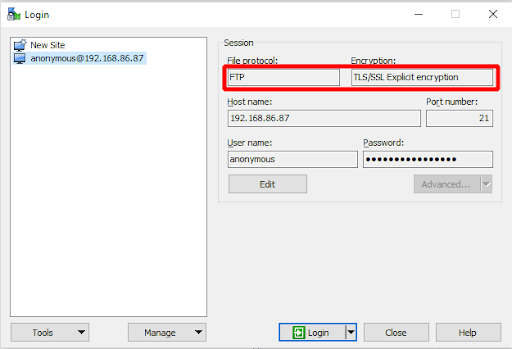
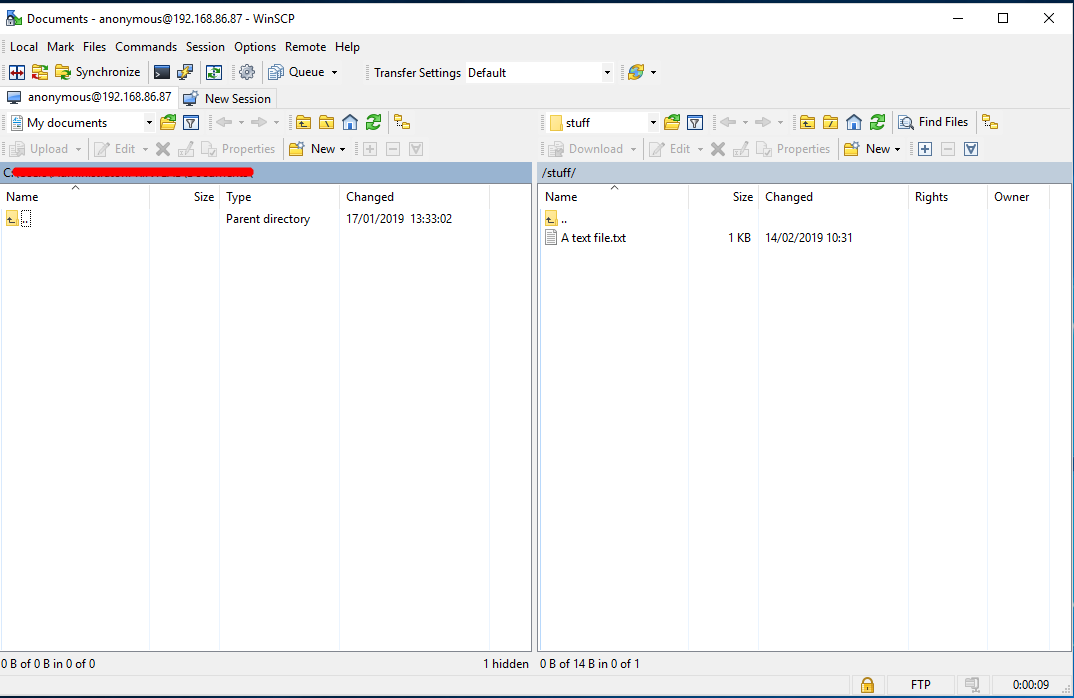
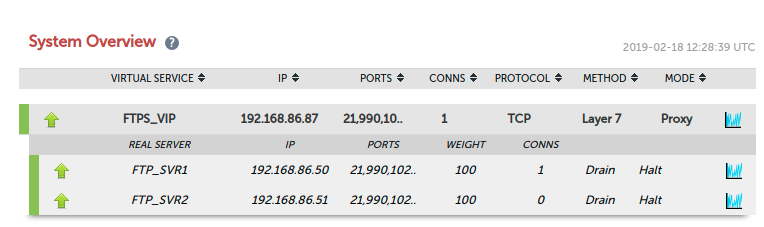
So there we have it: we’ve proven that FTPS implicit and explicit can be load balanced and all in one encompassing VIP. Happy days!
However there is one thing to be aware of
SSL offloading for explicit FTPS is not supported by HAproxy and therefore is not a recommended configuration. The reason for this is that explicit FTPS requires STARTTLS meaning that the connection starts as clear text and then upgrades to TLS. To be compatible with STARTTLS you will need to use the TCP mode configuration.

