Is getting an A+ rating with the Qualys scanner starting to feel a bit like chasing a mythical unicorn? Every time you get close to catching and keeping the beast — it run's away and they change the rules again!

I’ve been testing again whilst also looking at the effect of FIPS compatible ciphers. Loadbalancer.org has lots of government customers using FIPS compliance mode, so it makes sense to re-evaluate our current cipher recommendations. Although to be honest I agree with Microsoft — that FIPS is to be used with caution.
Spoiler alert you CAN'T GET A+ on Qualys with FIPS
You can only officialy get an A- :-(. But if your willing to tweek the ciphers and bend the rules a tiny bit you can push it up to an A+...
I've worked hard to offer you some sensible recommendations that mitigate common known vulnerabilities scoring the best scores from Qualys while maintaining maximum client support.
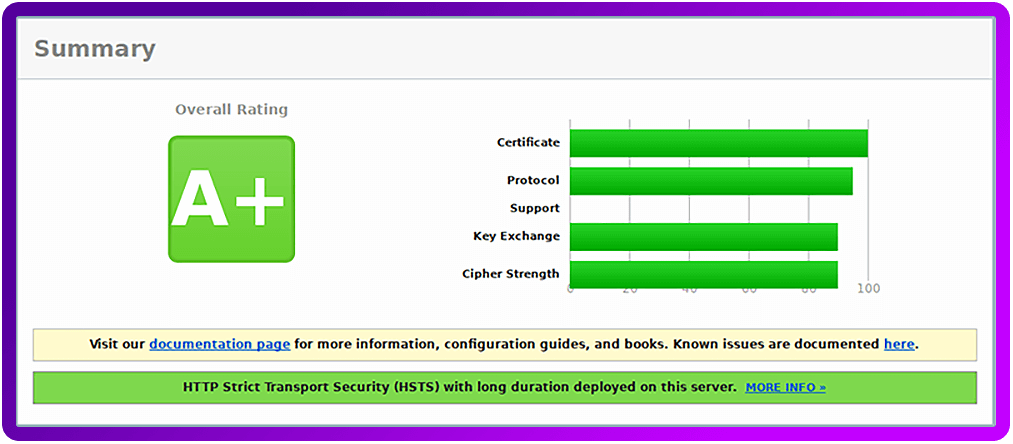
Before I get into the ciphers let me first point out that to get an A+ you not only need a secure list of ciphers but at least a 6 month HSTS header otherwise the best you can achieve is an A. Luckily we can insert this at L7 for you so you’ll likely need to enable this if seeking that top score. What on earth is a HSTS header I hear you cry, well it’s a way to tell your users browser not to talk over HTTP with your website for a specified amount of time. This is an attempt to protect from man-in-the-middle attacks for conforming browsers.
More info on HTTP Strict Transport Security.
Back to the ciphers, I’ll start with our favourite short succinct list which we used to achieve the A+ shown above, it's made with ciphers exclusively from the FIPS supported list and offers fairly reasonable client support if you can leave TLS1.0 enabled:
ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DHE-RSA-AES256-SHA256
Here is an example configuration file, its based on an STunnel v5.33 build with OpenSSL 1.0.2j-fips:
# STunnel configuration file generated by Loadbalancer.org appliance
# Written 2017-05-10 13:41
setuid = stunnel
pid = /var/run/stunnel/stunnel.pid
socket = a:IP_FREEBIND=yes
fips = yes
[VIP_Name]
cert = /etc/loadbalancer.org/certs/VIP_Name/VIP_Name.pem
ciphers = ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DHE-RSA-AES256-SHA256
accept = 0.0.0.0:443
connect = 127.0.0.1:80
delay = yes
options = NO_SSLv2
options = NO_SSLv3
options = CIPHER_SERVER_PREFERENCE
options = DONT_INSERT_EMPTY_FRAGMENTS
renegotiation = no
TIMEOUTclose = 0
The default options we use here are quite important for stopping various man-in-the-middle attacks like POODLE and BEAST etc.
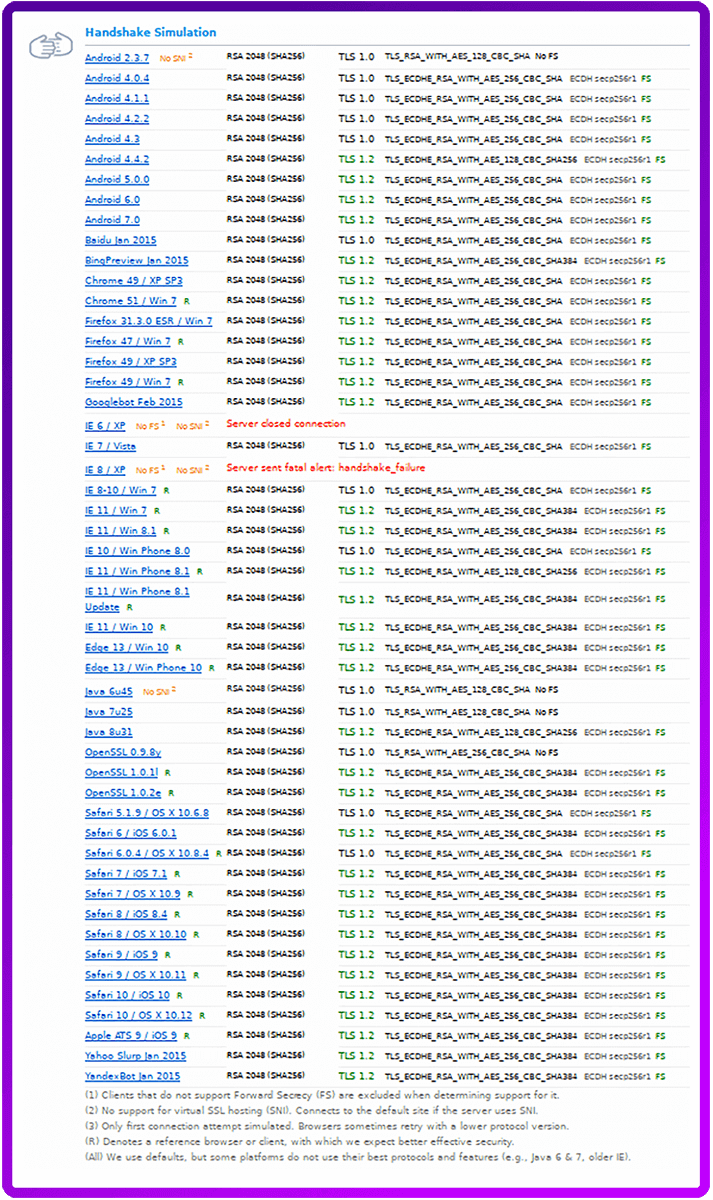
So what does a simulated handshake tell us about this configuration?
Well no Windows XP for a start... but otherwise it looks pretty good...
Supported Server Cipher(s):
- Accepted TLSv1 256 bits ECDHE-RSA-AES256-SHA
- Accepted TLSv1 256 bits AES256-SHA
- Accepted TLSv1 128 bits AES128-SHA
- Accepted TLS11 256 bits ECDHE-RSA-AES256-SHA
- Accepted TLS11 256 bits AES256-SHA
- Accepted TLS11 128 bits AES128-SHA
- Accepted TLS12 256 bits ECDHE-RSA-AES256-SHA384
- Accepted TLS12 256 bits ECDHE-RSA-AES256-SHA
- Accepted TLS12 256 bits DHE-RSA-AES256-SHA256
- Accepted TLS12 256 bits AES256-SHA256
- Accepted TLS12 256 bits AES256-SHA
- Accepted TLS12 128 bits ECDHE-RSA-AES128-SHA256
- Accepted TLS12 128 bits AES128-GCM-SHA256
- Accepted TLS12 128 bits AES128-SHA256
- Accepted TLS12 128 bits AES128-SHA
Preferred Server Cipher(s):
- TLSv1 256 bits ECDHE-RSA-AES256-SHA
- TLS11 256 bits ECDHE-RSA-AES256-SHA
- TLS12 256 bits ECDHE-RSA-AES256-SHA384
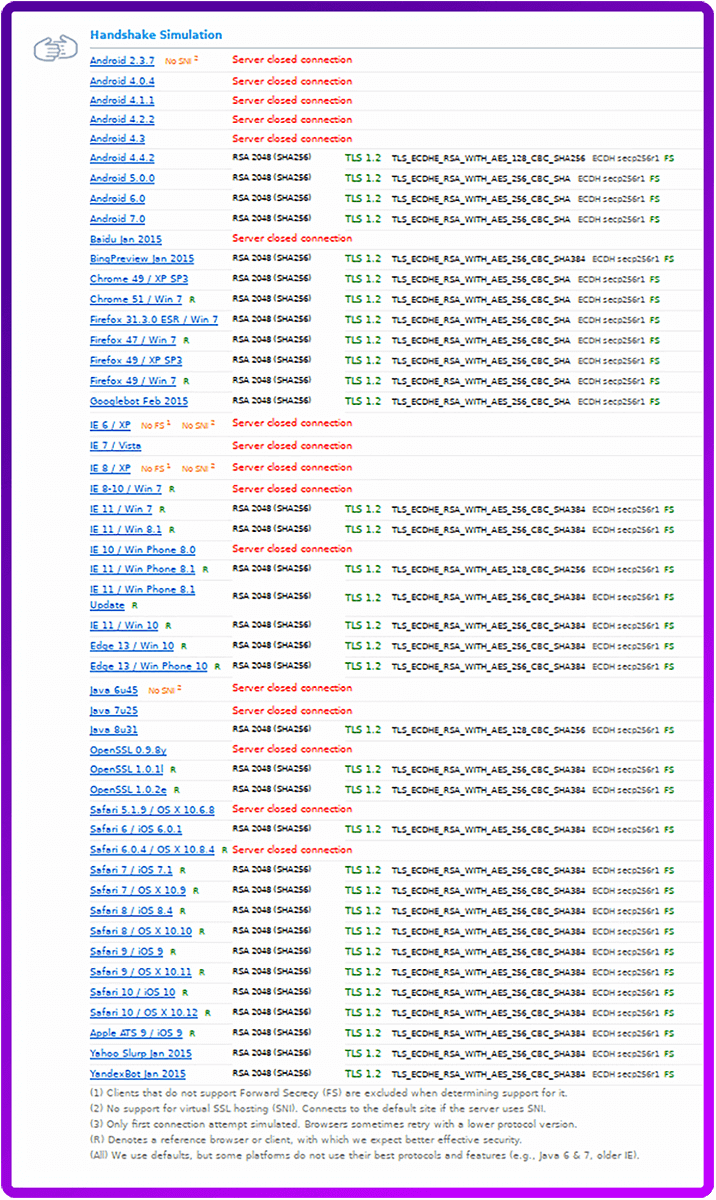
We also have a fair number of customers disabling TLS1 due to upcoming PCI changes.
It will also still support all modern operating systems and browsers even if you need TLS1.0 disabled but some older products will obviously fail to negotiate a connection (Possibly a good thing…).
If you disable TLSv1 you get the following handshake:
Supported Server Cipher(s):
- Accepted TLS11 256 bits ECDHE-RSA-AES256-SHA
- Accepted TLS11 256 bits AES256-SHA
- Accepted TLS11 128 bits AES128-SHA
- Accepted TLS12 256 bits ECDHE-RSA-AES256-SHA384
- Accepted TLS12 256 bits ECDHE-RSA-AES256-SHA
- Accepted TLS12 256 bits DHE-RSA-AES256-SHA256
- Accepted TLS12 256 bits AES256-SHA256
- Accepted TLS12 256 bits AES256-SHA
- Accepted TLS12 128 bits ECDHE-RSA-AES128-SHA256
- Accepted TLS12 128 bits AES128-GCM-SHA256
- Accepted TLS12 128 bits AES128-SHA256
- Accepted TLS12 128 bits AES128-SHA
Preferred Server Cipher(s):
- TLS11 256 bits ECDHE-RSA-AES256-SHA
- TLS12 256 bits ECDHE-RSA-AES256-SHA384
Next, comes my favourite list if you don't need FIPS only ciphers - I use this one myself!
ECDHE-RSA-RC4-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA:AES256-SHA:HIGH:!3DES:!RC4:!MD5:!aNULL:!EDH
Supported Server Cipher(s):
- Accepted TLSv1 256 bits ECDHE-RSA-AES256-SHA
- Accepted TLSv1 256 bits AES256-SHA
- Accepted TLSv1 256 bits CAMELLIA256-SHA
- Accepted TLSv1 128 bits ECDHE-RSA-AES128-SHA
- Accepted TLSv1 128 bits AES128-SHA
- Accepted TLSv1 128 bits CAMELLIA128-SHA
- Accepted TLS11 256 bits ECDHE-RSA-AES256-SHA
- Accepted TLS11 256 bits AES256-SHA
- Accepted TLS11 256 bits CAMELLIA256-SHA
- Accepted TLS11 128 bits ECDHE-RSA-AES128-SHA
- Accepted TLS11 128 bits AES128-SHA
- Accepted TLS11 128 bits CAMELLIA128-SHA
- Accepted TLS12 256 bits ECDHE-RSA-AES256-GCM-SHA384
- Accepted TLS12 256 bits ECDHE-RSA-AES256-SHA384
- Accepted TLS12 256 bits ECDHE-RSA-AES256-SHA
- Accepted TLS12 256 bits AES256-GCM-SHA384
- Accepted TLS12 256 bits AES256-SHA256
- Accepted TLS12 256 bits AES256-SHA
- Accepted TLS12 256 bits CAMELLIA256-SHA
- Accepted TLS12 128 bits ECDHE-RSA-AES128-GCM-SHA256
- Accepted TLS12 128 bits ECDHE-RSA-AES128-SHA256
- Accepted TLS12 128 bits ECDHE-RSA-AES128-SHA
- Accepted TLS12 128 bits AES128-GCM-SHA256
- Accepted TLS12 128 bits AES128-SHA256
- Accepted TLS12 128 bits AES128-SHA
- Accepted TLS12 128 bits CAMELLIA128-SHA
Preferred Server Cipher(s):
- TLSv1 128 bits ECDHE-RSA-AES128-SHA
- TLS11 128 bits ECDHE-RSA-AES128-SHA
- TLS12 128 bits ECDHE-RSA-AES128-SHA
This will also get you an A+ but offers additional ciphers not found on the FIPS list. These Camellia ciphers are considered about as strong as AES and come from Japan, you’ll see lots of these additionally enabled with the above cipher list in use.
More info on Camellia ciphers.
Another option is to use the full and complete FIPS list, but currently it will only give you an A- due to being capped. Annoyingly it’s a few reference browsers not negotiating a cipher that supports forward secrecy, however, client support is excellent and you can almost certainly expect that IE6 / WinXP client will work if they enable TLS1.0 support in IE.
ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:DHE-DSS-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA256:ECDH-RSA-AES256-GCM-SHA384:ECDH-ECDSA-AES256-GCM-SHA384:ECDH-RSA-AES256-SHA384:ECDH-ECDSA-AES256-SHA384:AES256-GCM-SHA384:AES256-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:DHE-DSS-AES128-GCM-SHA256:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DHE-DSS-AES128-SHA256:ECDH-RSA-AES128-GCM-SHA256:ECDH-ECDSA-AES128-GCM-SHA256:ECDH-RSA-AES128-SHA256:ECDH-ECDSA-AES128-SHA256:AES128-GCM-SHA256:AES128-SHA256:AES256-SHA:DES-CBC3-SHA:AES128-SHA
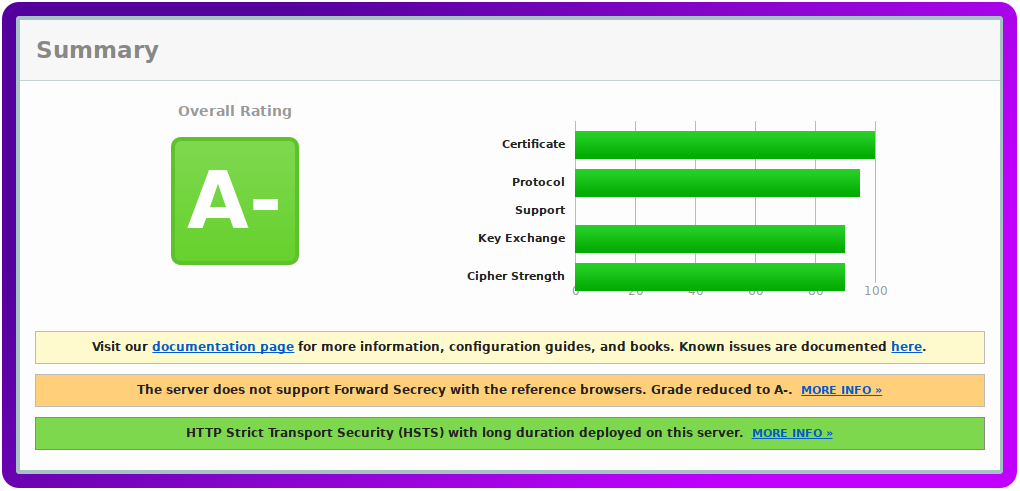
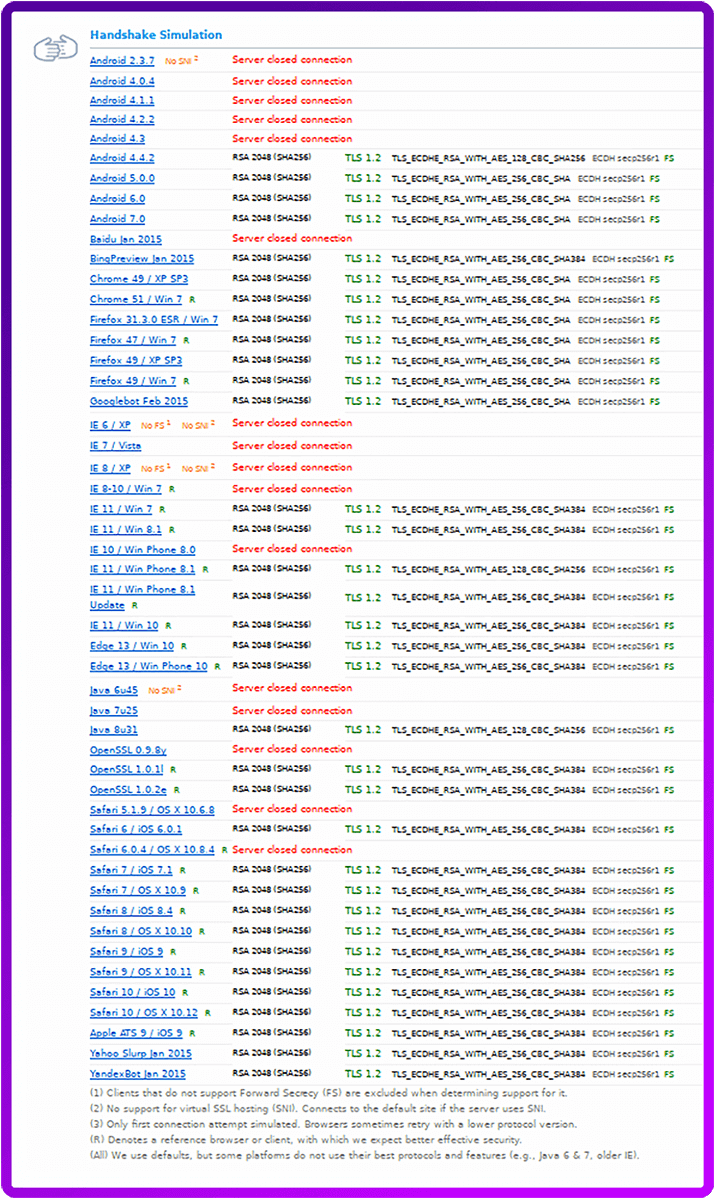
I’m sure that over time our recommendations will continue to evolve, security is as always a moving target with new vulnerabilities being discovered every day. Even ciphers we’ve come to know and trust like Arcfour and 3DES have recently fallen out of favour proving the need to constantly review your security.
Note for enabling TLS1.0 in IE6 - your only option if you need to get Windows XP clients to works with SSL.
If you open your IE Options, and under the 'Advanced' tab almost at the bottom you should find 'Use TLS 1.0' if you put a tick into this box you should find that with the Cipher we gave things start to work again.