Load balancing Microsoft IIS

Useful resources
About Microsoft Internet Information Services (IIS)
Microsoft Internet Information Services (IIS) is a high performance, flexible web server created by Microsoft for use with Windows. In order for web sites to remain available, IT managers will need to configure IIS server load balancing.
Key benefits of load balancing
Here are a few key benefits:
- Ensures the application is always available
- Provides a stable, optimal performance
- Ability to isolate servers which reduces risk when performing upgrades/maintenance
- Scalability
Loadbalancer.org supports Microsoft IIS with all common load balancing methods, incorporating numerous modifications and customisations to suit your requirements and can be deployed physically, virtually or in the cloud. Whatever your preference, we’ll ensure that your deployment is suited for your environment.
Microsoft’s Enterprise solutions are at the heart of businesses everywhere. Loadbalancer.org is officially certified for all of Microsoft’s key applications which you can find here. More details on the Microsoft IIS components, how it works, and prerequisites for load balancing can be found in our deployment guide, available to view below.
How to load balance Microsoft IIS
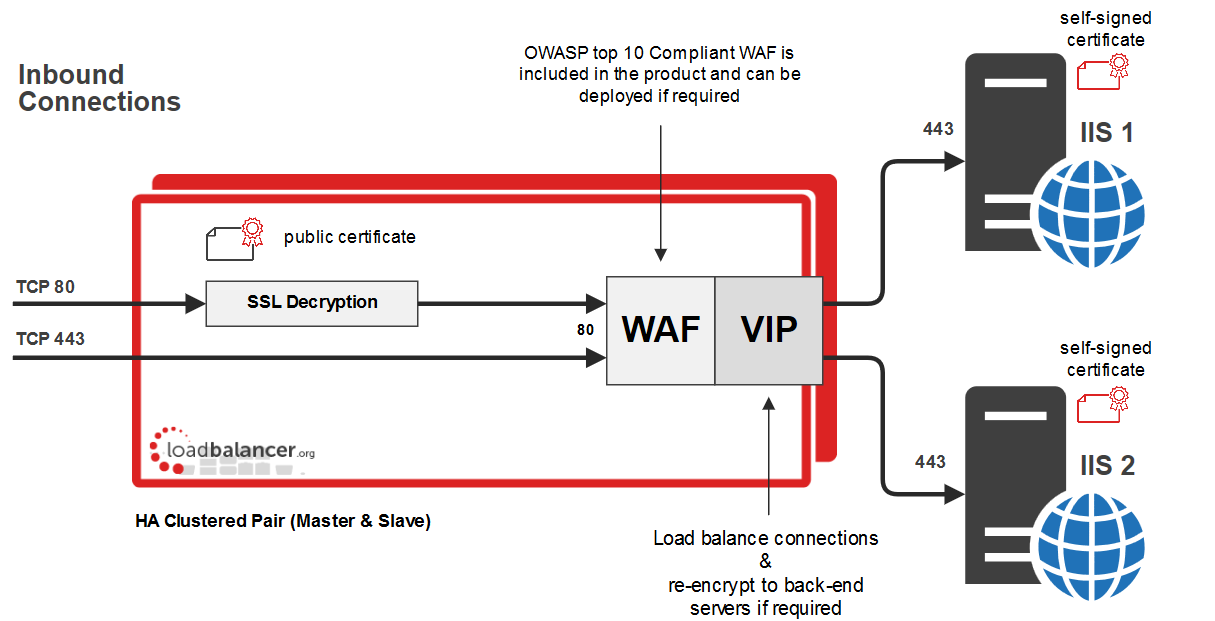
Example HTTPS deployment illustrating SSL termination, WAF traffic inspection and SSL re-encryption.
Protocols and load balancing methods for Microsoft IIS
| Protocol | Port | Load balancing methods |
| HTTP | 80 | Layer 7 SNAT (Recommended) Using Reverse Proxy mode is the easiest and most flexible load balancing method, offering advanced URL switching, cookie insertion and WAF capabilities.
Layer 4 DR Direct Routing has the advantage of being fully transparent and seriously fast but requires solving the arp problem. Layer 4 NAT Traditional NAT mode gives easy to implement fast and transparent load balancing but usually requires a two-arm configuration (two subnets). |
| HTTPS | 443 | All load balancing methods can be easily configured for SSL Pass-through.
This has the advantage of being fast, secure and easy to maintain. Identical SSL certificates will need to exist on each of your backend servers for pass-through security. SSL Termination or off-loading must be used when advanced Layer 7 functionality such as cookies or URL switching is required. You can also implement SNI if you have multiple domain certificates one one public IP address. Optional re-encryption is also available between the load balancer and IIS. |
| FTP | 20,21 | All load balancing methods can be easily configured for FTP. However the original design of FTP did not work well with firewalls so it was modified to add a special PASV (Passive) mode. If you are load balancing FTP we recommend that you configure PASV on the FTP server, or use Layer 4 NAT mode which handles the issue automatically. |
| SFTP | 21 | All load balancing methods can be easily configured for SFTP. |
guides

Microsoft IIS Deployment Guide
Read deployment guide
Web Servers with OWASP Top 10 WAF in AWS Deployment Guide
Read deployment guidemanual

Administration manual v8
Read manualblog

Using the X-Forwarded-For Header with Microsoft IIS
Read blogother

Build a web farm with IIS servers
Read other
Configure IIS web farm load balancing
Read other

