Load balancing Microsoft Exchange

Useful resources
About Microsoft Exchange
Microsoft Exchange Server, the mainstay of Microsoft’s Unified Communications solution, has grown beyond being regarded as the standard in business email into a fully-fledged communications tool. Exchange 2019 is Microsoft’s latest enterprise-level messaging and collaboration server – its architecture is very similar to Exchange 2016.
Key benefits of load balancing
Here are a few key benefits:
- Ensures the application is always available
- Provides a stable, optimal performance
- Ability to isolate servers which reduces risk when performing upgrades/maintenance
- Scalability
Microsoft’s Enterprise solutions are at the heart of businesses everywhere. Loadbalancer.org is officially certified for all of Microsoft’s key applications which you can find here. More details on the Microsoft Exchange components, how it works, and prerequisites for load balancing can be found in our deployment guide, available to view below.
How to load balance Microsoft Exchange
To implement highly available and scalable deployments of Microsoft Exchange Server, Microsoft recommends using a load balancer to distribute the traffic among multiple Exchange servers. Both current and legacy versions of Exchange support load balancing, with a different approach and recommendations dependent on the version you are running.
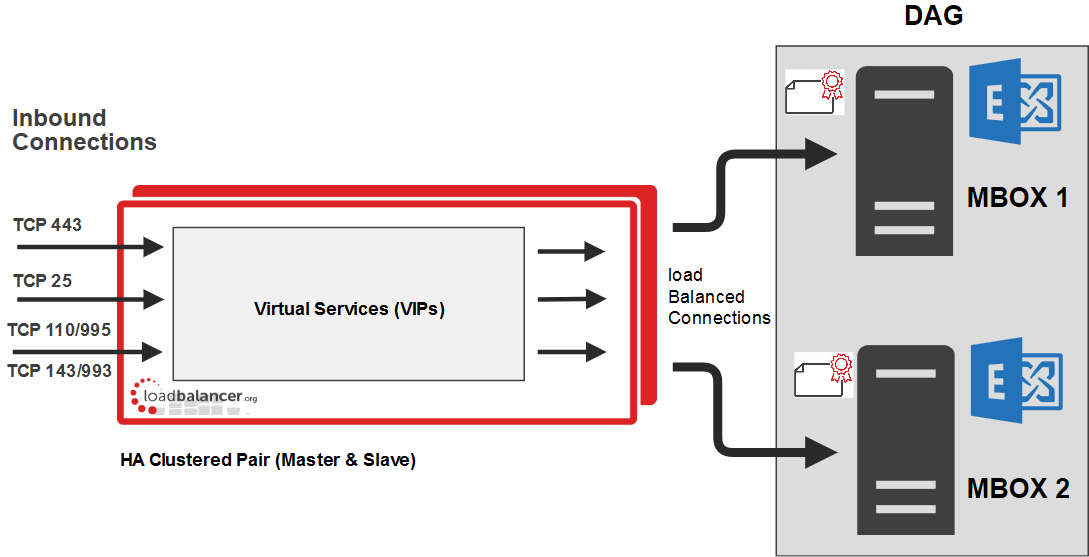
Example Exchange 2019 / 2016 deployment using a minimal 2 server setup.
The load balancer can be deployed in 4 fundamental ways: Layer 4 DR mode, Layer 4 NAT mode, Layer 4 SNAT mode and Layer 7 SNAT mode.
- For Exchange 2019, 2016 or 2010 we recommend using Layer 7 SNAT mode for simplicity
- For Exchange 2013, where possible we recommend Layer 4 Direct Routing (DR) mode
Exchange 2019, 2016 and 2013 Protocol Table
| Protocol | Role | Ports | Load balancing methods |
| TCP | CAS | 443 | Used for Outlook on the Web, AutoDiscovery, Web Services, ActiveSync, Outlook Anywhere, Offline Address Book, Exchange Administration Center). Layer 4 DR (Direct Routing – Ultra-fast, local server based load balancing) Layer 7 SNAT |
| TCP | CAS | 25 | Used for Inbound SMTP Layer 4 DR (Direct Routing – Ultra-fast, local server based load balancing) Layer 7 SNAT (Flexible, URL switching and cookie insertion capabilities) |
| TCP | CAS | 110,995,143,993 | Used for POP3 clients Used for IMAP4 clients Layer 4 DR (Direct Routing – Ultra-fast, local server based load balancing) Layer 7 SNAT (Flexible, URL switching and cookie insertion capabilities) |
Exchange 2010 Protocol Table
| Protocol | Role | Ports | Load balancing methods |
| TCP | CAS | 80 | Layer 7 SNAT |
| TCP | CAS | 443 | Layer 7 SNAT |
| TCP | HT | 25 | Used for the HT (Hub Transport) role Layer 4 DR (Direct Routing – Ultra-fast, local server based load balancing) Layer 4 NAT (Fast Load balancing throughput) Layer 7 SNAT (Flexible, URL switching and cookie insertion capabilities) |
| TCP | CAS | 110, 995, 143, 993, 135, 60201 | Used for POP3 clients Used for IMAP4 clients RPC endpoint mapper Static port for Exchange address book service Layer 7 SNAT |
guides

Microsoft Exchange 2019 Deployment Guide
Read deployment guide
Microsoft Exchange 2016 Deployment Guide
Read deployment guide
Microsoft Exchange 2013 Deployment Guide
Read deployment guide
Microsoft Exchange 2010 Deployment Guide
Read deployment guidemanual

Administration manual v8
Read manualcase study

BenQ - Load balancing Microsoft Exchange
Read case studyblogs

Load balancing Exchange 2016
Read blog
Load balancing Exchange 2013
Read blog
Load balancing Exchange 2010
Read blog
Exchange 2013 - Microsoft finally have an email solution designed for high availability and load balancing
Read blog
Load balancing Exchange 2010 CAS Array with HAProxy
Read blogother

Microsoft approved for load balancers for Exchange
Read other
TechGenix - Loadbalancer.org product review
Read other

