
How do I secure my load balancer with Active Directory, LDAP or RADIUS?
How-Tos Published on •4 mins Last updatedI’ve noticed a lot more of our customers are asking to use their Active Directory login details with the load balancer appliance. And it can get a bit fiddly, so I wanted to write a blog to explain the process in more detail.
Why use centralized authentication?
Better security, for a start. But most people love the fact that they just have one username and password to remember.
Any form of central authentication has the following benefits:
- Fewer logical accounts and physical devices to secure
- Easy to block user access instantly to thousands of devices
- Easy to create security groups with access profiles
- Easier to achieve compliance with regulations, HIPAA etc
System administrators are well aware that unfortunately some network appliances don’t support central authentication, or make it difficult to achieve.
Hang on, isn’t the load balancer secure already?
Yes. The built-in load balancer authentication is enough for most people and certainly still the recommended solution. It is robust, secure, and tried and tested. Although we do recommend that you treat the appliance as a single user bastion host (just like you would a firewall).
OK, I’m interested - so how does this work?
You’ll need to map an administrator login from your AD Domain controller to a user account on the load balancer. Then your level of access will be controlled by the local load balancer account - but the password policy and lock-out is managed by your single chosen network login.
The Loadbalancer.org appliance has a built-in script to help you configure centralised authentication. You’ll soon be able to log in using your Active Directory Domain username and password, or use other external authentication methods such as LDAP or RADIUS.
Let’s get started
You’ll need console access to the load balancer - usually it's easiest to log in using SSH. Once you have opened an SSH session to your appliance, follow these simple steps:
-
Type “lbauthconfig” and press Enter
-
You should now see the following screen:
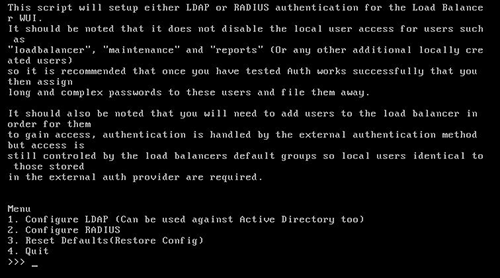
In this example, I'm using Option 1 - Configure LDAP
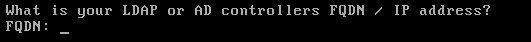
- Next, you will be asked to input your LDAP FQDN or IP address:
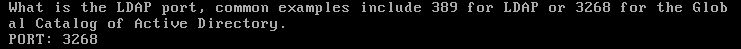
- Next you will need to specify your LDAP Port - typically these are Port 389 for LDAP & 3268 for the Global Catalog of Active Directory.
- On the next option,you will need to specify your AD Username in the form of USER@DOMAIN - this does not need to be a privileged user.

- Next you will be asked to enter the password for the above AD account:

- Once you have entered your password, you will be required to enter NETBIOS DC domain name:
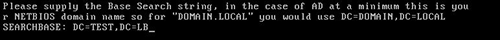
-
From the next menu, you can select the attribute to authenticate against. In my example I will use “samAccountName”.
-
This will now prompt you for the first user and their password.
-
Once this has been completed, you should now be able to open up your browser and type in the IP address of your appliance on port 9443 and it will prompt you for the username and password. This is where you can now log in using your Active Directory username and password:
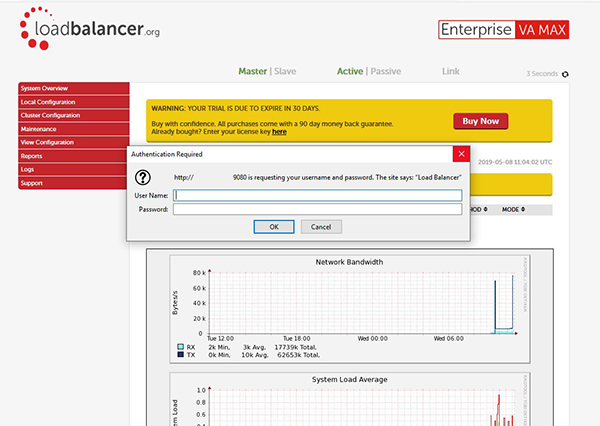
- Now that we've configured access to the domain controler for the first user, it's easy to add as many users as you like through the normal part of the web interface i.e. Maintenance > Passwords . Just make sure you tick the AD auth option for each one:
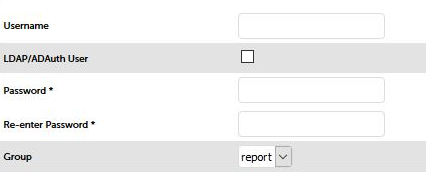
Hang on, I don’t like it - how do I turn AD authentication off again?
That's OK, we can part as friends:
-
Simply open up a putty session to your loadbalancer appliance and log in as “root” credentials.
-
Now type lbauthconfig and press “Enter”.
-
You should now see a screen like below:
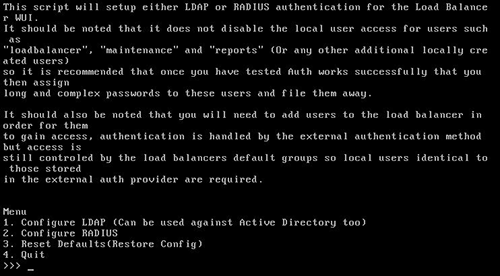
-
Now select option 3 and press enter.
-
Once this runs through its process, you will then see the following message:
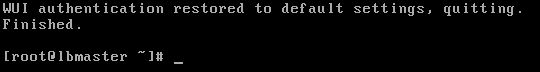
- You can now log out of the cli shell. Then perform a Ctrl+F5 in your browser and you will be able to log in to the appliance as the default loadbalancer credentials.
So, should I use centralized authentication for my load balancers?
If your environment requires that extra level of security or you just like the sound of having a single login, then why not?
I’ve always thought that good technology should make your life easier, and this latest feature in the load balancer will certainly help to do that.
If you have any questions about the above, please don't hesitate to get in touch.
